Cwtch /kʊtʃ/
Cwtch (/kʊtʃ/ - a Welsh word roughly translating to “a hug that creates a safe place”) is a decentralized, privacy-preserving, multi-party messaging protocol that can be used to build metadata resistant applications.
Participants in Cwtch can host their own safe spaces, or lend their infrastructure to others seeking a safe space. There is no “Cwtch service” or “Cwtch network”. The Cwtch protocol is open, and anyone is free to build bots, services and user interfaces and integrate and interact with Cwtch.
All communication in Cwtch is end-to-end encrypted and takes place over Tor v3 onion services.
Cwtch has been designed such that no information is exchanged or available to anyone without their explicit consent, including on-the-wire messages and protocol metadata.
How it Works
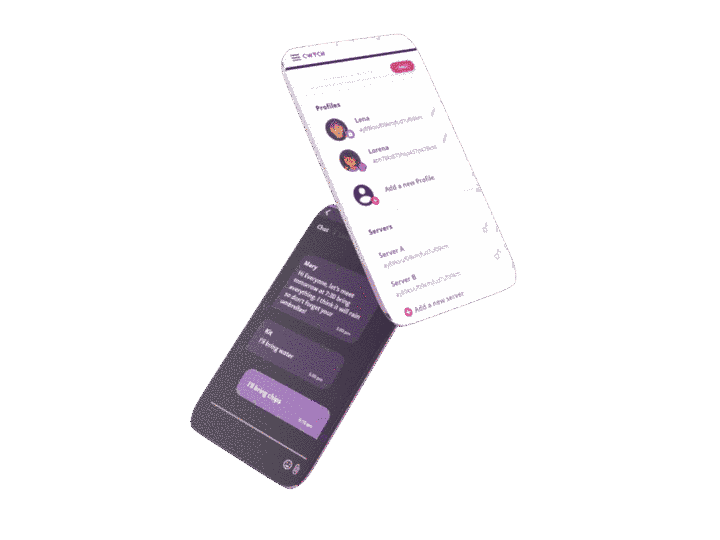
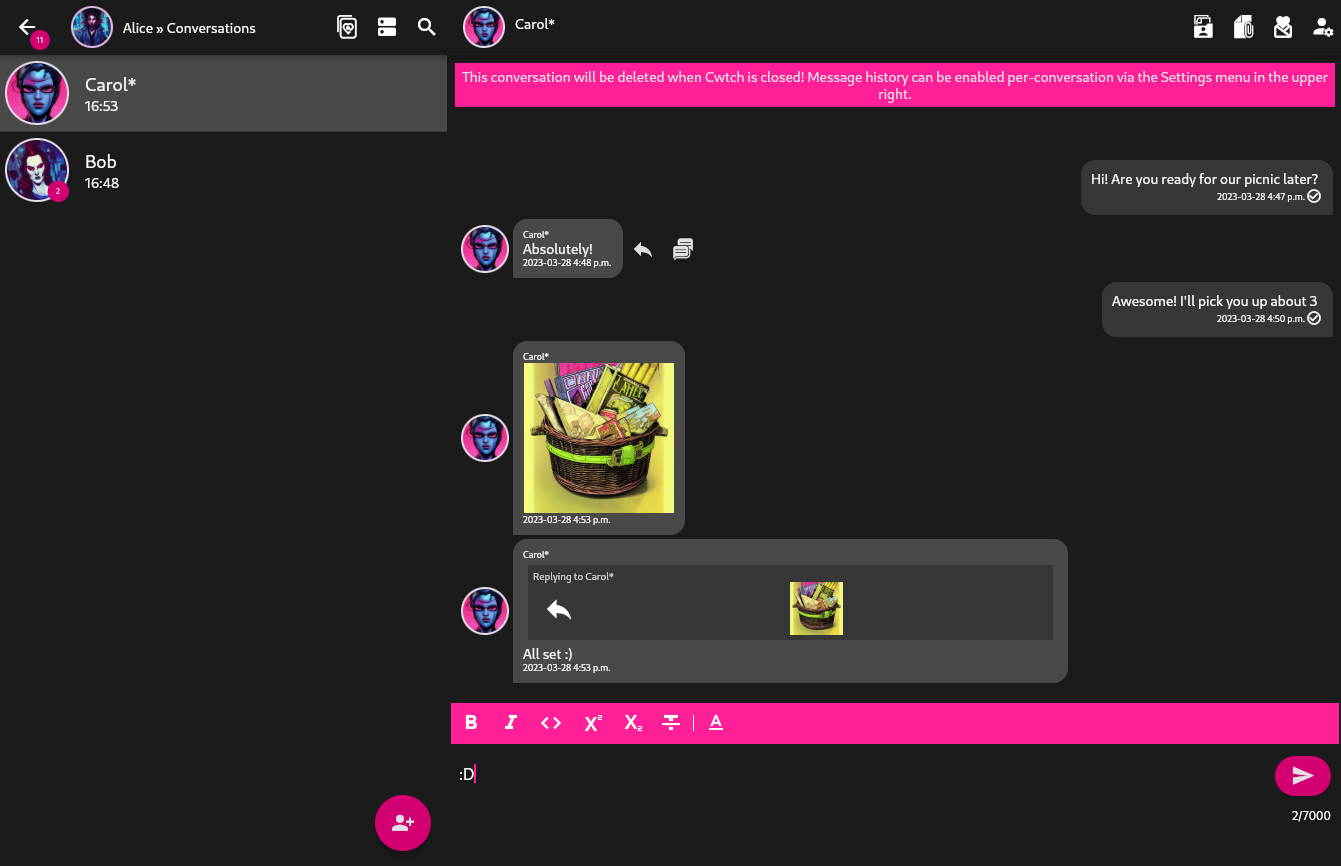
Screenshots
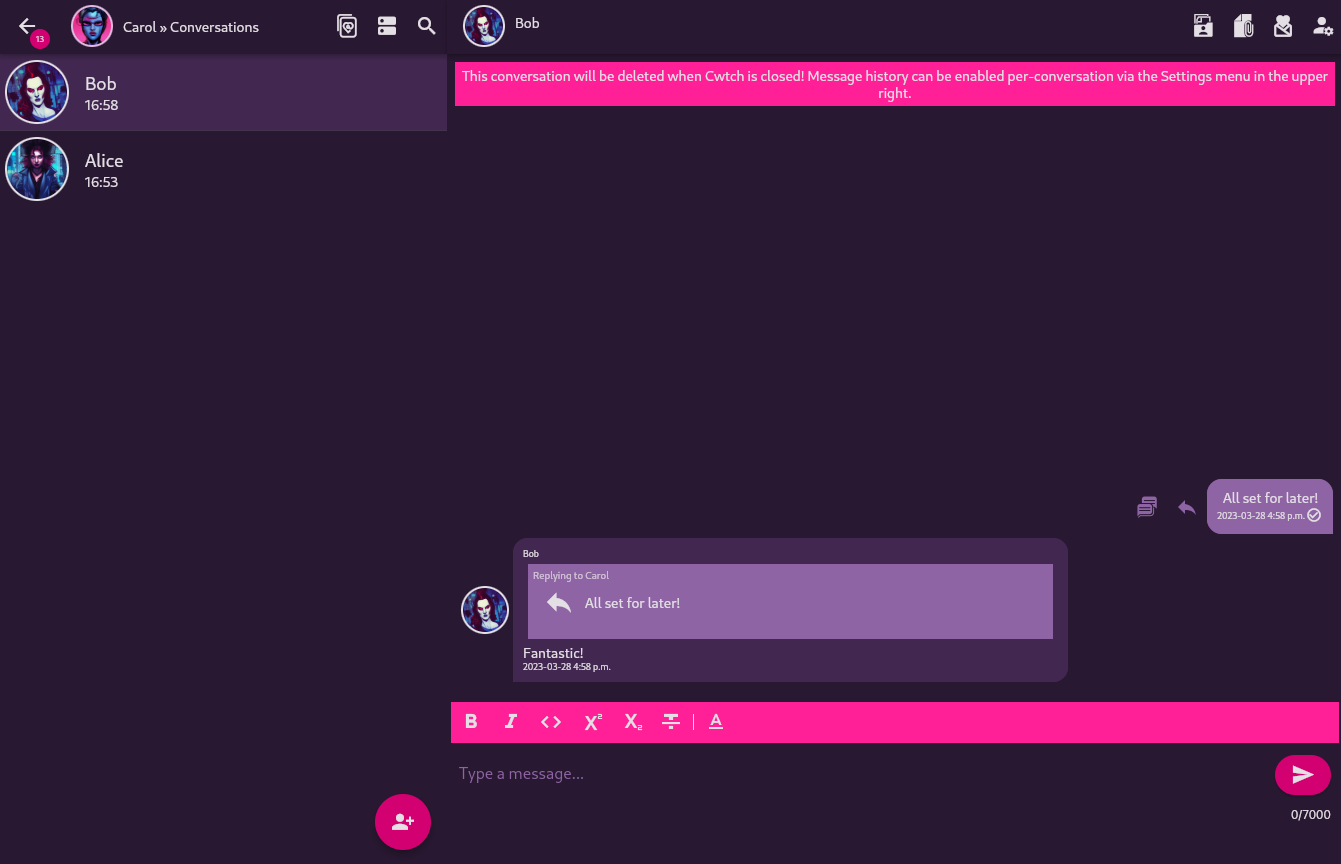
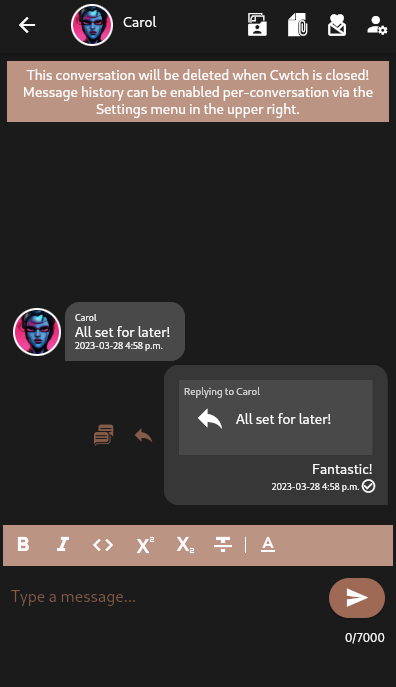
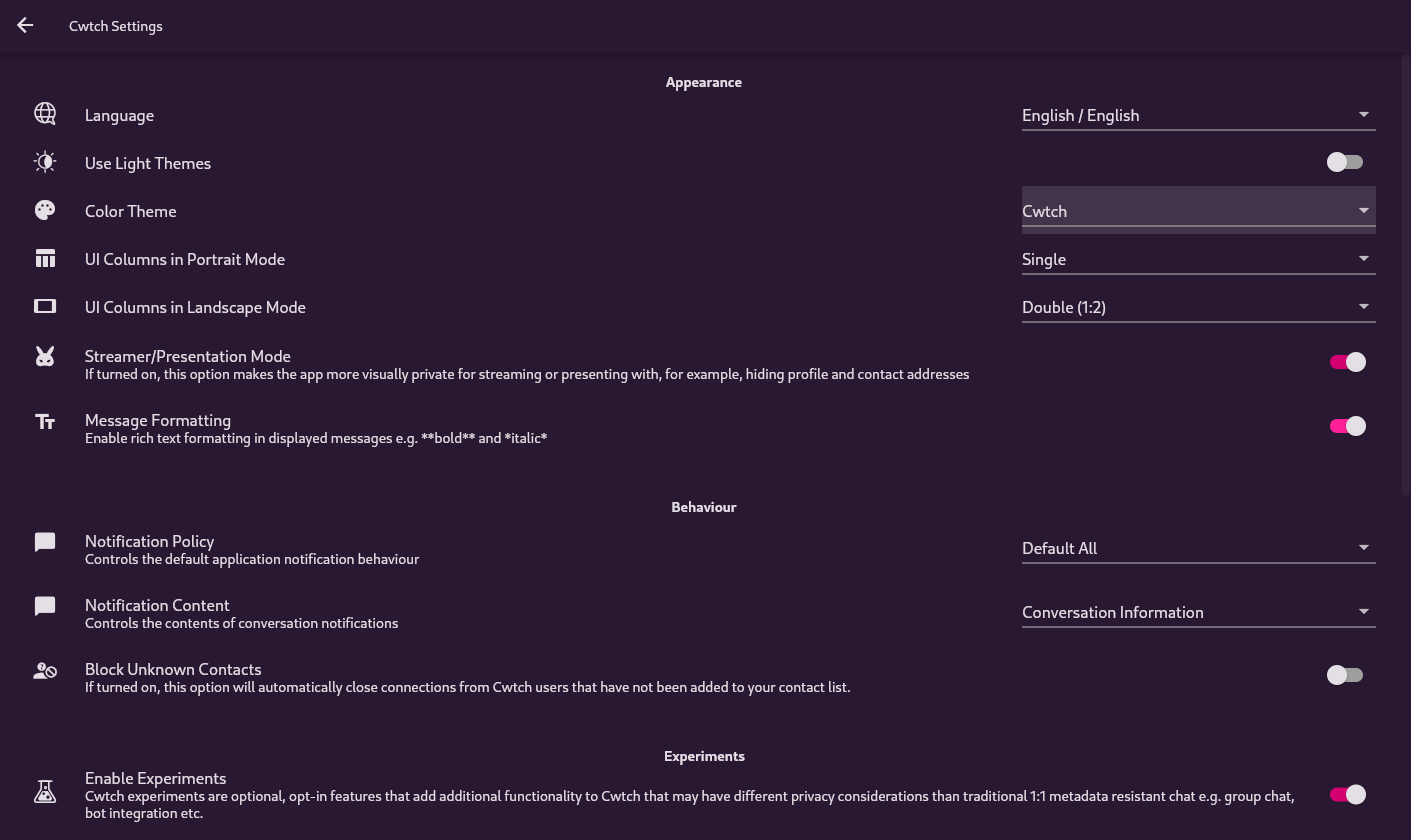
FAQ
How is Cwtch different to Signal / Whatsapp / iMessage?
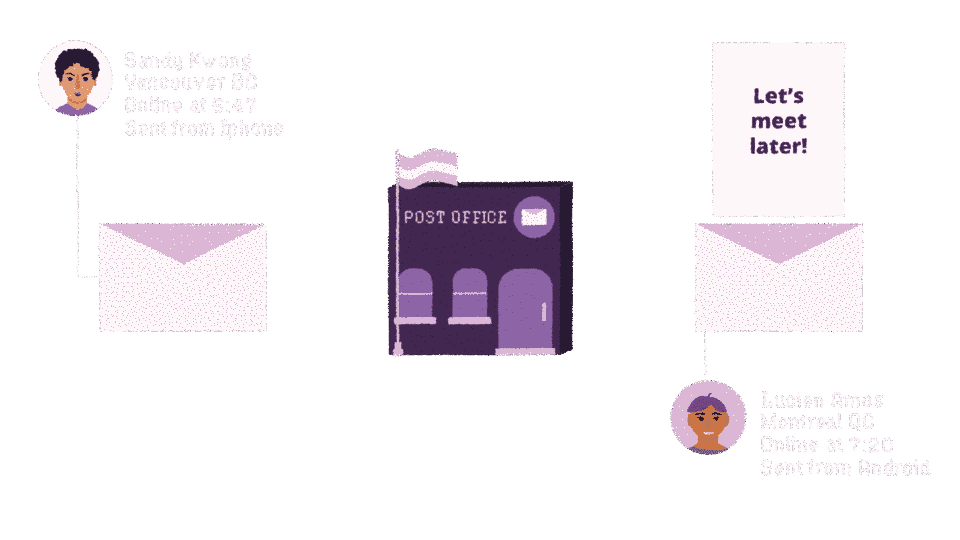
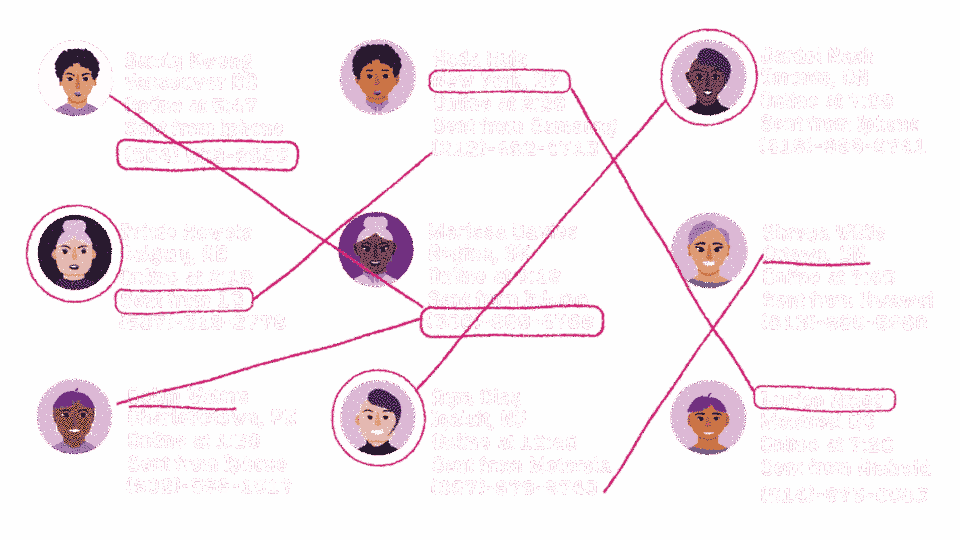
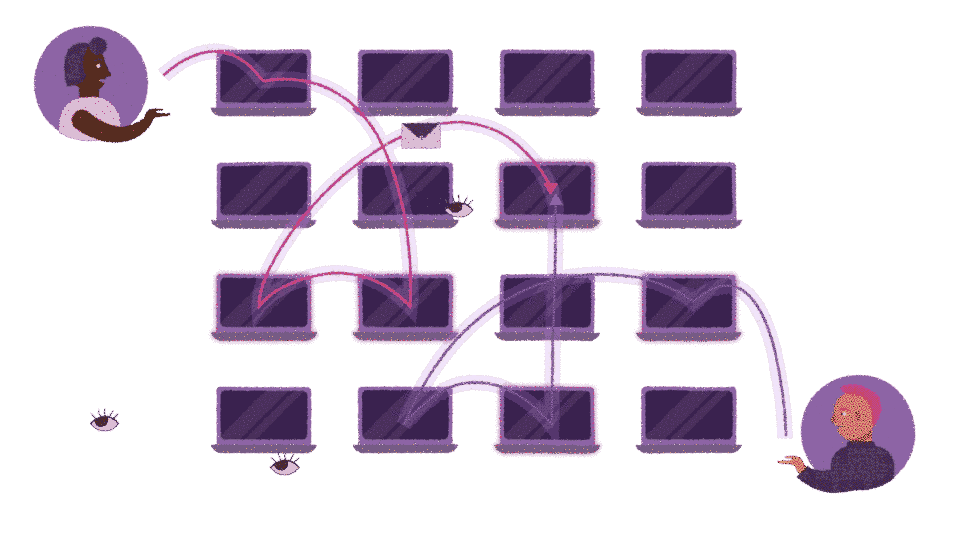
Cwtch is decentralized and focused on metadata-privacy in addition to communications privacy. Unlike other communication platforms, none of your messages are routed through a centralized server that has access to metadata such as your social network of friends, or who sent and received a particular message.
Even in experimental group chats which do rely on a routing server, the server learns no information about which messages belong to which group, who is a member of which group, or who messages are intended for.
We believe that our tools should help people resist surveillance. Communications metadata is known to be exploited by many adversaries to undermine the security of systems; to track people; and to conduct large scale social networking analysis that feeds into mass surveillance systems. And because of that, we explicitly designed Cwtch for metadata privacy.
How do I pronounce Cwtch?
Like "kutch", to rhyme with "butch".
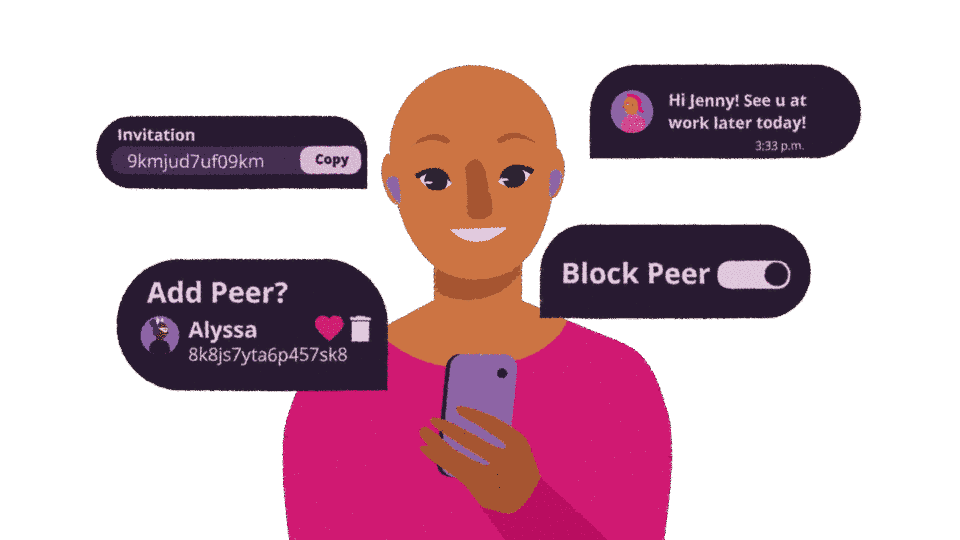
What is the difference between a peer-to-peer connection and a cwtch group?
Cwtch peer-to-peer connections allow 2 people to message each other directly. Behind the scenes peer-to-peer connections use Tor v3 onion services to provide an encrypted, and metadata resistant connection. Because of this direct connection, both parties need to be online at the same time in order to message each other.
Cwtch Groups allow multiple parties to participate in a single conversation using an untrusted server (that can be provided by 3rd party or self hosted). Server operators cannot learn how many people are in a group, or what is being discussed. If multiple groups are hosted on a single server then the server is unable to learn which messages belong to which group without the collusion of a group member. Unlike in peer-to-peer conversations, group conversations can be conducted asynchronously, so everyone in a group doesn't need to be online at the same time.
Why are cwtch groups experimental?
Metadata-resistant group messaging is still an open problem. While the version we provide in Cwtch Beta is designed to be secure and metadata private it is rather inefficient and can be misused. As such we advise caution when using it, and only provide it as an opt-in feature.
What happens if I forget the password to an encrypted profile? Or uninstall the application? Or delete my profiles folder?
Unlike a traditional centralized service that can offer password overrides, Cwtch stores all your data locally on your device.
Without the password, and the encrypted file, it is practically impossible for anyone to derive the key to decrypt the profile. As such that profile should be considered irretrievably lost.
How can I run my own Cwtch Server?
The reference implementation for a Cwtch server is open source. Anyone can run a Cwtch server, and anyone with a copy of the server key bundle of public keys can host groups on that server without the operator having access to group related metadata.
Why does Cwtch use data when I'm not using it?
At startup Cwtch launches a Tor process so that it can setup and connect to v3 onion services.
All Cwtch activity takes place through these onion services, and are reliant on Tor, we setup Cwtch in a background service that can be managed by Androids lifecycle management and can be reconnected to the foreground application when it is unpaused, or restarted.
Without this background process management Cwtch would require Tor to be reinitialized every time the app is loaded which would make it slow to start, and would make peer connection unusable on Android, as everytime the app went away you would go offline.
Note: Group connections are synchronized every time cwtch is online and it is not necessary to be online all the time when using them.
When a Tor process is running it will download some amount of data in order to retrieve consensus from the Tor network. Any active onion services will also require a small amount of data to maintain their circuits and introduction points independent of any app use.
In the future we plan to allow cwtch clients to opt-in to using an external Tor connection such as Orbot to manage Tor processes separately from Cwtch.
How can I shutdown Cwtch?
The front-pane of the app has a "Shutdown Cwtch" button (with an 'X') icon. Pressing this button will trigger a dialog, and on confirmation Cwtch will be shutdown and all profiles will be unloaded.
How can I get involved in testing Cwtch?
For information on the libraries, protocol, threat model and open questions please check out the Cwtch Security Handbook.
FuzzBot is our development testing bot. You can add FuzzBot as a contact: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad .
Sending Fuzzbot the command testgroup-invite will cause FuzzBot to invite you to the Cwtch Testers Group!
For more information on FuzzBot see our Discreet Log development blog.
How can I get involved in supporting Cwtch?
- Report Bugs and Issues and Feature Requests: https://git.openprivacy.ca/cwtch.im/cwtch-ui/issues
- Submit Pull Requests: https://git.openprivacy.ca/cwtch.im/cwtch-ui
- Volunteer to Translate: Contact team@cwtch.im to be added to our Lokalise translation team. We currently have translations for the following languages (help for other languages/locales welcome)!
- Brazilian Portuguese (100% Translated)
- Dutch (100% Translated)
- English (100% Translated)
- French (100% Translated)
- German (100% Translated)
- Italian (100% Translated)
- Polish (100% Translated)
- Russian (100% Translated)
- Spanish (100% Translated)
- Welsh (100% Translated)
- Danish (89% Translated)
- Norwegian (89% Translated)
- Romanian (89% Translated)
- Luxembourgish (26% Translated)
- Greek (19% Translated)
- Portuguese (16% Translated)
- Donate to Open Privacy Research Society to help us fund the development of new features!